Hackers fast to take advantage of fears created by celebrity nude photo leak
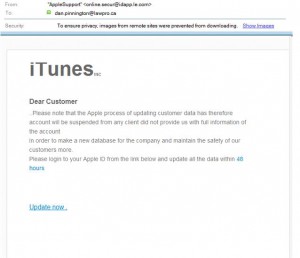
This morning I got the following email, purportedly from Apple Support, telling me to take steps to update my Apple ID information:
It is a text book example of a phishing scam – the very type of scam that was likely used for tricking some of the celebrities caught in the nude photo leak into disclosing their personal account login information to hackers. (see this Verge article for a detailed timeline and explanation on how the celebrity nude photo leak likely happened.)
Wow – that didn’t take long. Here the hackers are taking advantage of fears created by celebrity nude photo leak to frighten people into disclosing their AppleID login information. Goes to show you the ingenuity and determination of hackers.
“Phishing” is one of the most common scams that cyber criminals use because it can produce spectacular results with very little effort or expense on the part of the hacker. Phishing involves the use of an email, text message or phone call that appears to come from a trusted source, vendor or company you usually deal with, but is actually from a third-party impostor. Phishing messages are intended to trick you into giving cyber criminals your information by asking you to update or confirm personal or online account information. Personal information and identity theft and/or payment scams are the motives behind most phishing scams. Millions of people are phished on a daily basis, and while most don’t fall for it, criminals only need a few dupes to make it pay off. See this article for examples of common phishing scam messages.
Cyber criminals do their best to make phishing messages look official and legitimate. They will mimic real communications from the company or entity they are supposedly from by using the same layout, fonts, wording, message footers and copyright notices, etc. as official messages. They will often include corporate logos and even one or more links to the alleged sender’s real website. To make it more likely you will fall for the scam, phishing messages commonly involve urgent scenarios. They may suggest that you must reset your password because your account has been compromised by hackers or they may request that you login to your account to review an invoice or deal with an outstanding payment.
Another common phishing scam is a call from someone claiming to be from Microsoft who will tell you your computer is infected and that you must go to a special website to download an update that will fix the problem. Phishing scams can also be a request to complete a survey or to give information to collect a prize you have won. They can also be requests for money supposedly from someone you know.
Many phishing messages will include a link or attachment that you are asked to click so you can update your information. After doing so, the webpage or attachment you will see (which will also have text and logos to make it look official) will prompt you to enter your name, account number, password and other personal information – thereby giving it to cyber criminals.
To make matters worse, clicking on links or attachments in phishing messages often causes malware to be downloaded to your computer as well.
Don’t let this happen to you. Learn how to spot phishing messages so you don’t fall for this scam. Phishing scams work because some people are gullible. If you get a phishing message from a bank and you don’t have an account there, you aren’t likely to fall for the scam. However, if you have an account at that bank, the message may look legitimate to you and you are more likely to fall for the scam. Here are some clues that can help you recognize a phishing message:
- The link you are asked to visit is different from the company’s usual website URL (see the next paragraph).
- The displayed email address is different than the actual sender’s address. See the message above: The displayed name is AppleSupport, but if you look at the actual email address you see it is [email protected]. This is, of course, done intentionally to trick you.
- The main part of the sender’s email address is not the same as the company’s usual email address (see the email address in the previous bullet point).
- Bad spelling and poor grammar. See the above message (e.g., no end punctuation, sentences are worded in funny way).
- The promise of receiving money or another big prize.
- Anyone asking for money – even if you know them.
Checking the link you are asked to go to is one of the best ways to confirm that a message is a phishing scam. Place your mouse over the link you are asked to go to (but don’t click on it!) and look at the taskbar in your browser window (usually at the lower left). It will show you the URL of the link. It should start with the proper characters in the proper website (e.g., lawpro.ca) and not a URL that appears unrelated (e.g., 12.67.876/aed/1234/bnklogin). An unrelated URL virtually guarantees it is a phishing scam. Watch for small differences: “lawpro.com.tv” seems close, but is different! This is the URL the “Update now” link takes you to in the message graphic (it certainly isn’t an Apple website):
Never respond to “phishing” requests for personal information in the mail, over the phone or online. Most importantly – this is probably the most common way that personal information is stolen – never ever reply to unsolicited or suspicious emails, instant messages or web pages asking for your personal information (e.g., usernames, passwords, SIN number, bank account numbers, PINs, credit card numbers, mother’s birth name or birthday), even if they appear to be from a known or trusted person or business. Legitimate businesses should never send you an email message asking to send your username, password or other information to them in an email message. If in doubt, call the company yourself using a phone number from a trusted source. Don’t use the number in the email – it could be fake too!
Portions of this article originally appeared in the December 2013 “Cybercrime and Law Firms” issue of LAWPRO Magazine . See the original article for some examples of common phishing scam messages. The other articles in the magazine have a lot more advice and information about how to protect yourself from cybercriminals and hackers.

September 04, 2014 at 1:45 pm, liz said:
This is why it’s important that we are proactive in educating ourselves as well as our family and friends on these threats to our financial and personal security. I’ve read tons of reports on different scams at Callercenter.com and while most of those who received the call got away without losing money to the scammer, there were a few who did and had to start from scratch again. It was just terrible.