Protecting Yourself from Cybercrime Dangers: Address security vulnerabilities by installing operating system and program updates
Cybercrime dangers are many, complex and ever-changing. Hardly a day goes by without another news report of a data breach or other cyber-related scam or theft. Cyber criminals have considerable resources and expertise, and can cause significant damage to their targets. Cyber criminals specifically target law firms as law firms regularly have funds in their trust accounts and client data that is often very valuable. LAWPRO encourages all law firms to make dedicated and ongoing efforts to identify and understand their potential cybercrime vulnerabilities, and to take steps to reduce their exposure to cyber-related dangers. This article, from the December 2013 issue of LAWPRO Magazine, reviews the specific cybercrime dangers law firms need to be concerned about, and how they can mitigate their risks.
There are millions of lines of computer code in the operating systems and programs that run on your
computers, tablets and smartphones. These operating systems and programs will have hundreds or even thousands of settings and features. These settings and features are intended to allow you to do all the things you want to on these different devices.
Amongst all these settings and features, cyber criminals look for “exploits.” An exploit is a particular setting, feature or sequence of commands that will cause an unintended or unanticipated behaviour to occur on a computer or other device. Exploits create security vulnerabilities because cyber criminals can use them to open a backdoor to your network, allow malware to run, or do other damaging things. New exploits are discovered on a weekly or even daily basis.
Updates
When an exploit is discovered, software companies quickly rewrite their code and release updates or patches to stop the exploit from working. To protect against newly discovered exploits, devices must be updated with the latest versions of operating systems and programs.
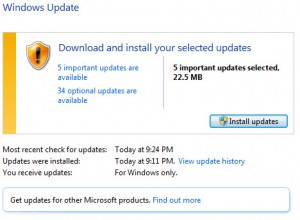
To keep your computers and other devices safe, you should be checking for and installing updates regularly, ideally on a weekly basis. This is particularly the case for Microsoft products, which are prone to security vulnerabilities. While not as prone to vulnerabilities as Microsoft products, Apple products should be updated regularly as well. Don’t forget to update the other non-Microsoft or non-Apple software running on your devices. Sometimes direct links to an updates webpage can be found on the Help menu. Otherwise, you should be able to find the software product’s site with a search on Google.
If you are using Windows XP or Office 2003, note that Microsoft will no longer be supporting these products as of April 8, 2014. Using these products after this date will expose you to greater security dangers.
Automatic updates
Enabling automatic updates can help keep your computers and other devices up-to-date. Both Windows and Apple operating systems have an “automatic update” feature that automatically notifies you when updates are available for your devices. Once activated, the device will periodically check for updates. Available updates will be downloaded, and depending how you configure things, installed with or without your knowledge. Some people prefer to set the automatic updates feature to ask for permission to install updates to avoid problems that might arise due to an update installation.
Others prefer to have updates installed without intervention from the computer user (this can help make sure updates get installed). The Ninite.com site can help Windows computer users check for and install updates (for free). Note, in some firms individual users will have no control over updates as the installation of updates will be centrally controlled and managed. The paid version of Ninite can be used for this purpose for Windows computers.
Back up before you install updates
It is very important to remember that installing updates can unintentionally interfere with the way your computer/device or individual programs/apps operate. It is possible that a program/app may not operate properly or at all, that data could be lost, or that a device will fail to restart after an update is installed. Creating a restore point (a temporary backup of your configuration and data) and/or making a proper backup of all the programs and data on a device before you install updates can help you recover if there are unanticipated problems.

Leave a Reply